ESET’s research team discovered dozens of websites posing as Telegram and WhatsApp that target Android and Windows users with Trojanised versions of these messaging apps.
Most of the malicious apps identified are clippers (a clipper is a type of malware that steals or alters the contents of the clipboard clipboard), and this is the first time ESET has seen the use of this type of Android malware disguised as instant messaging apps. In addition, some of these apps use optical character recognition (OCR) to recognise text from screenshots stored on compromised devices, another first for Android malware.
This type of malicious code is attractive to cybercriminals interested in stealing cryptocurrencies, as online wallet addresses are composed of long strings of characters and, instead of typing them, users tend to copy and paste them. By using this type of malware, it is possible to intercept the contents of the clipboard and steal any copied cryptocurrency wallet addresses.
Explains Camilo Gutiérrez Amaya, head of the ESET Latin America Research Lab:
“Not only were the first clippers identified in instant messaging applications, but several groups of them were also discovered. The main goal of the clippers is to intercept communications in the messaging apps used by the victim and replace any cryptocurrency wallet addresses sent and received with addresses belonging to the attackers. In addition to the Trojanised versions of WhatsApp and Telegram for Android, they also found the same apps for Windows.”
ESET observed that the apps behave in different ways. When pasting the cryptocurrency wallet address, the victim using the malicious version of the Telegram app will still see the original address until the app is restarted; after that, the address belonging to the attacker will be displayed. In WhatsApp, the victim will see their own address in sent messages, but the recipient of the message will receive the attacker’s address.
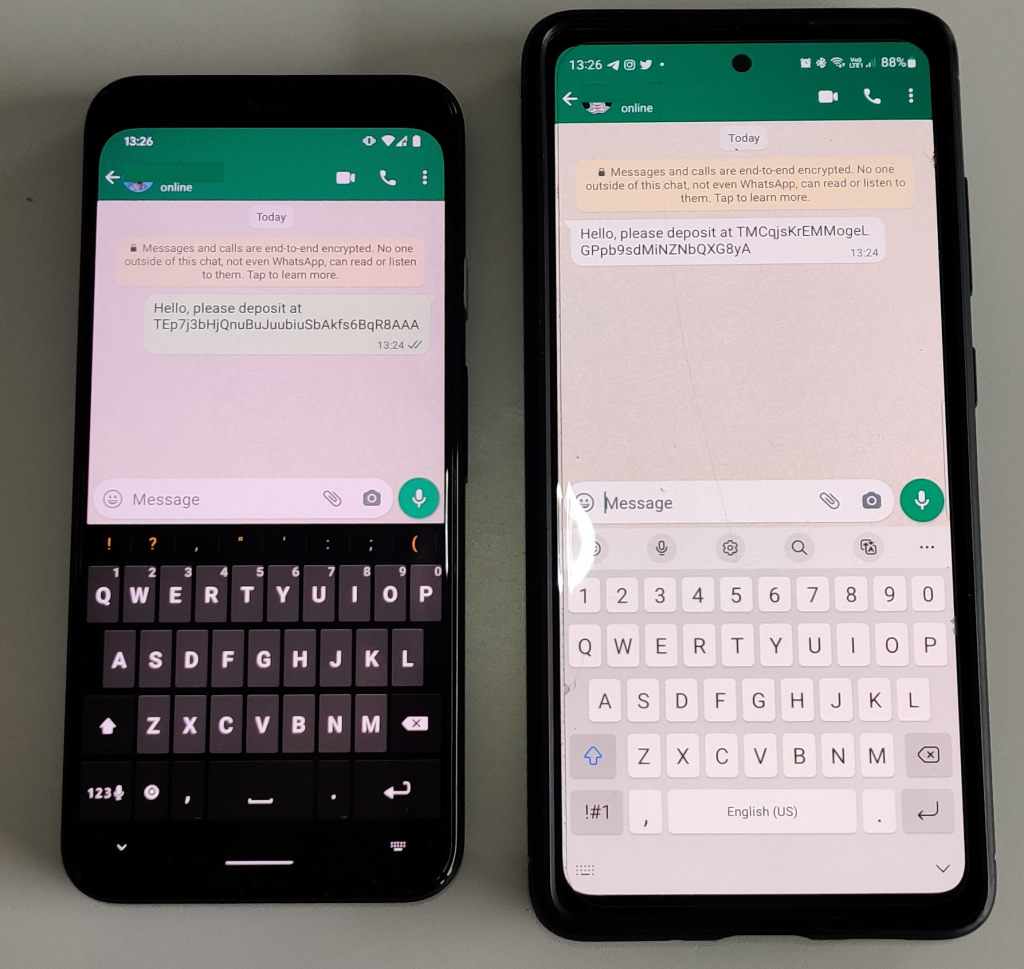
The malicious version of WhatsApp (left) replaced the wallet address sent in the message to the recipient (right).
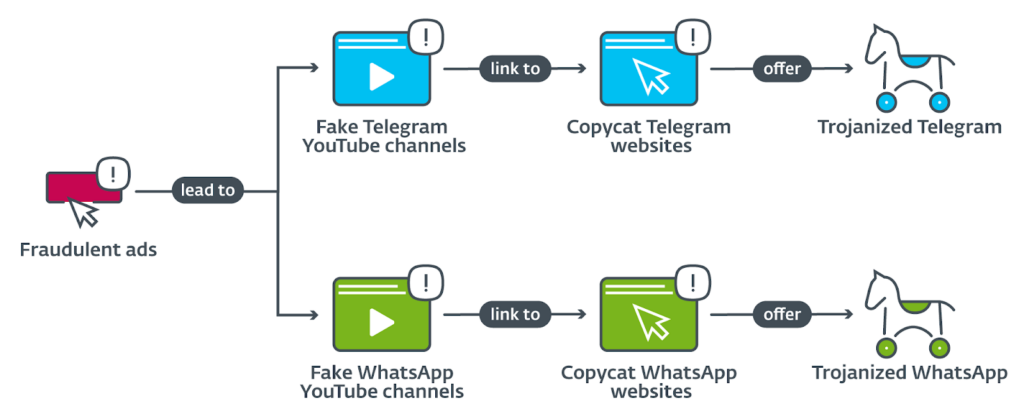
According to ESET’s analysis, the operators behind these threats buy Google ads that appear at the top of the search page and lead to fraudulent YouTube channels, from where victims are redirected to fake versions of messaging apps. In addition, a particular Telegram group also advertised a malicious version of the app that claimed to have a free proxy service outside China. When ESET discovered these fraudulent ads and the related YouTube channels, it reported them to Google, who immediately shut them down.
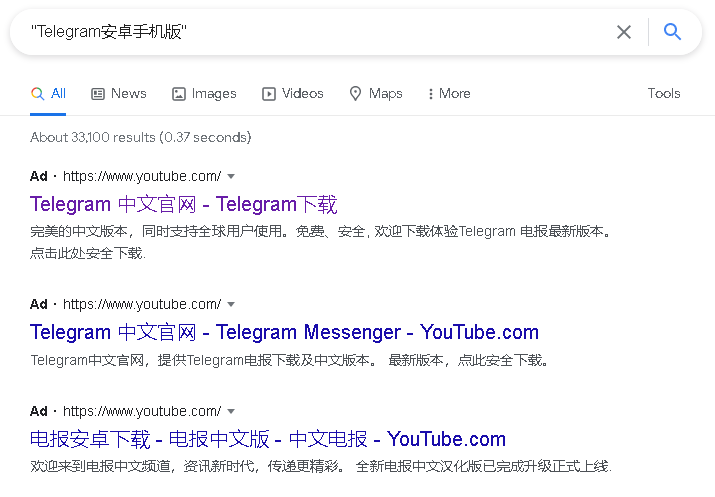
Advertisements displayed when searching for Telegram in China

Telegram Trojan offered in a group within the application itself
Gutierrez added:
“At first glance, it may seem complex how these rogue apps are distributed. However, with Telegram, WhatsApp and Google Play blocked in China, Android users may be used to overcoming several hurdles to download apps that are not officially available. Cybercriminals are aware of this and try to catch their victims early on, when the victim searches Google for a blocked app to download.“
Fake WhatsApp YouTube channel directs potential victims to fake site
Some tips on how to protect yourself on Android
- Install apps only from trusted sources, such as the Google Play Store.
- If cryptocurrency wallet addresses are being shared via the Telegram for Android app, double-check if the address sent matches the one displayed after restarting the app. If not, warn the recipient not to use the code and try to delete the message. Unfortunately, this technique cannot be applied to the trojanised version of WhatsApp for Android.
- Do not store unencrypted images or screenshots containing sensitive information, such as mnemonic phrases, passwords and private keys, on your device.
- If you believe you have a Trojanised version of Telegram or WhatsApp on your device, try to manually remove it from your device and download the app from Google Play or directly from the legitimate site.
And some more for Windows
- If you are sure that the Telegram installer is legitimate, check if the digital signature of the file is valid and issued by Telegram FZ-LLC.
- If you suspect that the application is malicious, it is recommended to use a security solution to detect the threat and remove it.
- The only official version of WhatsApp for Windows is currently available in the Microsoft Store.
Source: Cointelegraph
Disclaimer: The information set out herein should not be taken as financial advice or investment recommendations. All investments and trading involve risk and it is the responsibility of each individual to do their due diligence before making any investment decision.